Breaking through censorship barriers, even when Tor is blocked

Download video | view on YouTube
While Tor Browser provides many security and privacy properties and features, not everyone around the world has the luxury to connect to use it. By default, Tor Browser makes all of its users look alike by spoofing UserAgent (and other methods) to avoid fingerprinting attacks. However, it doesn't hide the fact you're connecting to Tor, an open network where anyone can get the list of relays. This network transparency has many benefits, but also has a downside: Many repressive governments and authorities benefit from blocking their users from having free and open access to the internet. They can simply get the list of Tor relays and block them. This bars millions of people from access to free information, often including those who need it most. We at Tor care about freedom of access to information and strongly oppose censorship. This is why we've developed methods to connect to the network and bypass censorship. These methods are called Pluggable Transports (PTs).
Pluggable Transports are a type of bridge to the Tor network. They take advantage of various transports and make encrypted traffic to Tor look like not-interesting or garbage traffic. Unlike normal relays, bridge information is kept secret and distributed between users via BridgeDB. If you're interested in helping censored users, you can become a bridge operator. And if you're a developer and have interesting ideas on how to make new PTs or want to contribute code, we've some good documents to get you up to speed.
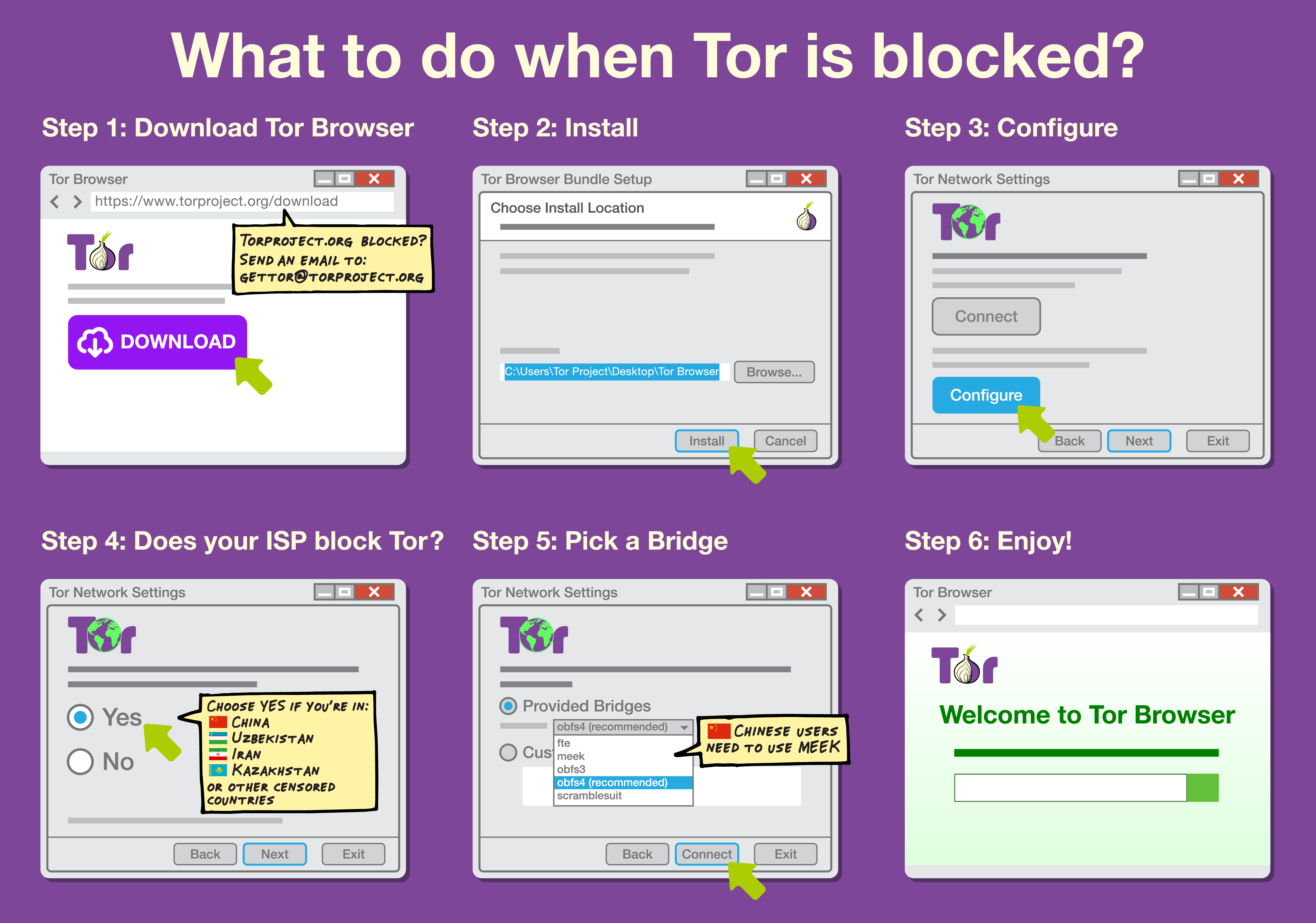
And finally, if you're a censored user and want to take advantage of PTs, I've good news for you. They're already included in Tor Browser and this how-to graphic should help you configure it to bypass censorship.
And of course we didn't forget to make a gif version:
In case you need more bridges, send an email to bridges@torproject.org or visit BridgeDB website.
At the end, I'd like to thank all anonymous contributors and Vivido Studio for making this work possible.
In solidarity,
Nima Fatemi

Comments
Please note that the comment area below has been archived.
Good stuff! Indeed, China's
Good stuff!
Indeed, China's (& Russia's) censorship is a huge problem - I daily deal with it.
Perhaps you could post these simple instructions in both of those languages? Or do you have the confidence that English is a sufficient vehicle for such a purpose?
Please be also advised that you should have any translations made verified by at least five unrelated individuals.
It's not unknown for some mischievous government agent to make use of such a translation opportunity by also inserting a 'hidden' message threatening any Chinese or Russian user 'new' to the Tor browser.
Here is a guide in the
Here is a guide in the Chinese language:
下载 Tor Browser 及 签名文件
Well, let us all then hope
Well, let us all then hope and trust that the disenfranchised bulk of the Chinese population - around 1.34 billion persons or 96% - will now, somehow, find your link on this here mrphs's blog.
Or perhaps you'll be kind enough to post it on Weibo and other Chinese network links?
Please also be aware that the Tor Browser is only 100% secure/safe when used on the Tor network so don't be getting yourself into any trouble by thinking its usage on other networks is also secure.
You may, of course, post your link in the comments section of any China related article found on economist.com. It won't be deleted - in my experience, I hasten to add - and it generally has a high Chinese readership.
There are, of course, also Chinese government agents using economist.com who will insult and vilify you knowing that The Economist staff will delete obnoxious remarks.
That's how Chinese and Russian censorship works on media they have no control of. LOL
Sadly, this means that your post too will consequently be deleted but The Economist staff will advise and apologise instantly to you via email and invite you to re-post your link.
Persevere. Never falter.
Thank you for your attention.
It's not a good idea that
It's not a good idea that posting it in public community or website in China,because goverment will arrest people who upload or sent these software.It's not safe for normal people
Strict-Transport-Security:
Strict-Transport-Security: The site specified a header that could not be parsed successfully. pluggable_transports-animation.mp4
No bridge: First hop will
No bridge: First hop will change with New Identity, New Tor Circuit for this Site. First hop is random from set of entry guards. Set will not change. Correct?
With bridge: Bridge will not change with New Identity, New Tor Circuit for this Site. Obfs4 (recommended) is set of 17 bridges. Why only use same 1 bridge for days, weeks?
Thank you.
Does using pluggable
Does using pluggable transports protect me against correlation attacks, or at least makes them significantly more difficult?
will you please to be fair ?
will you please to be fair ? most of blogs & website & mailing list are censored _ china& russia&turquey are far less censored than eu-uk-fr but it is unpleasant to admit it : you cannot read or write that you want , it is yet a colony of usa and it is worse than the others exotics countries.
Since I installed the latest
Since I installed the latest TOR update i get always connected to the same entry server in sweden whose ip is 155.4.59.251. Why is it so?
That is your entry guard and
That is your entry guard and it is normal.
There's a ticket about improving the way the guard is presented in the interface: #16665.
For a different question the
For a different question the FAQ says "When you use Tor the IP address you connect to changes at most every 10 minutes, and often more frequently than that." Should be updated since really only the middle and exit relays change every 10 minutes.
https://sedvblmbog.tudasnich.de/PT
https://sedvblmbog.tudasnich.de/PT - url from the video currently unfunctional?
Thanks for letting us know.
Thanks for letting us know. The correct URL is https://sedvblmbog.tudasnich.de/PT/ (with an / at the end). I'll open a ticket to fix it.
Why is not bridges used as
Why is not bridges used as default? Are it bacause of any disadvantages or is it less secure in some cases or something?
Why do you prefer mp4
Why do you prefer mp4 instead of webm?
I used tor browser and
I used tor browser and someone told me that it is used to change ip address constantly. is this true?
"While Tor Browser provides
"While Tor Browser provides many security and privacy properties and features, not everyone around the world has the luxury to connect to use it."
That is so true. Another truth is that not everyone in the world has the opportunity to buy (decreasing) Tor supported hardware. But that connects to a lost discussion about wealth.
Even the suggested alternative Tails is not that ideal. Although they do a very good job, it's a hard search for the right usb sticks or frustrating work to get a dvd working, and it just won't on systems too.
Therefore I'm using an old Torbrowser right now, a browser that still works on the machine with an older fine working operating system.
Luckily I don't get prisoned for using Tor because it is still legal to use this browser over here (yet) and there is also not many malware for my system.
Security issues : The thing I want to warn you about is that I see a growing number of ip addresses that are not part of Tornetwork but are interfering while Torbrowsing. Brazil is one of the countries as a result of iplookups.
I experience a growing number of 'onion with red cross errors' on the atlas check pages and it is then that I found out that the Torbutton don't warn you for a broken Tornetwork when it is already blinking for an available update with the yellow sign.
So, although I know I better should not use an old version of Torbrowser (The only alternative is not using Tor then), I think it's worth to look at the Torbutton issue just because it can happen that even people with almost new Torbrowsers often do not immediately update their Torbrowser and then do not notice when they are on a compromised connection because they do not get Warned by Torbutton that is overbusy with other warning blinking.
But maybe it is not an issue at all because it is fixed in your 6 series?
I hope so.
In the meanwhile I'll will keep being busy breaking through non Torsupport barriers voluntarily testing your network with my 'happy' 'HoneyTorpotbrowser'.
Keep up the good work and don't follow mozilla in their fashionable dropping support modus the next months, because in large parts of the world people just cannot afford new computers (get inspired by your own gif, the country list should then be longer though).
Tor Browser works on
Tor Browser works on hardware started from Pentium Pro. What is your case that you have to use an older version?
While these features are
While these features are great to circumvent censorship on ISP level they are useless when more and more websites are completely blocking tor users. Half of the internet appears to be behind cloudflare already and many more sites block all exit nodes by default.
What does the tor project intend to do against this form of censorship?
We've heard about raising awareness and seeking dialogue with site owners for years but things have only gotten worse. Services like cloudflare will never treat tor traffic the same way as regular users. It would be against their business model. We have to acknowledge that to the average webservice blocking all tor traffic to prevent vandalism is way more important than losing a few legitimate users.
I do understand that many people refuse to let tor users to edit or publish content on their sites, we all know where this often leads to, but they could at least let us view their sites.
So in the end I see two options:
1) Leave things as they are and accept that tor users will only have access to a limited and ever shrinking part of the internet and will be almost completely excluded from actively contributing
2) Think of a way to circumvent the preemptive exclusion of all tor users, maybe something like exit bridges. However I do agree there must be some mechanism to deter spamming and vandalism or at least makes it more difficult and less attractive. No idea how though.
I don't have a good answer
I don't have a good answer for you, but here are some pages to read on the subject.
List of services blocking Tor
A big list of web sites that block Tor users. (Mostly excludes CloudFlare sites, because there are too many.)
Differential Treatment of Anonymous Users
A research paper that measures how common it is for Tor users to be blocked
FAQ: You should hide the list of Tor relays, so people can't block the exits.
"There are a few reasons we don't: ..."
Using "exit bridges" as you suggest might not work, because many services (including CloudFlare) don't block Tor using a blacklist of exit nodes, rather have some automated system that detects abuse (like comment spam) and blocks IP addresses when it gets too high. (See the CloudFlare support page, Does CloudFlare block Tor?)
There are a few CloudFlare-hosted sites that have unblocked Tor users by whitelisting the "T1" country code; see https://trac.torproject.org/projects/tor/wiki/doc/CloudflareSites.
Why aren't pluggable
Why aren't pluggable transports available on the 2nd and 3rd relays as on the 1st relay?
Usually the censorship of
Usually the censorship of Tor happens close to the user, somewhere between the user and their bridge. So you only need a disguised connection on the first hop.
Maybe someday things will change, and pluggable transports will be needed for the connections between relays, but it's not needed today.
In Russia a majors email
In Russia a majors email providers are Russian: mail.ru and yandex. Also foreign email providers (and any other "information distribution platforms" are liable to move their servers into Russia, or they will be blocked. Google already aggreed. Using mail controllable by authorities allows them to replace your mails with own and in this way violate confidentiality and detect users avoiding censorship and jail them.
hi russianin you can use
hi russianin
you can use onion email providers and recommend your friends to do so.
or a harder way is to use *nix way and send your mail directly to the recipient! who enforces you to use "majors email providers" anyway? anyone can have directly accessible (onion) address. tip - you can even have several for distinct recipients.
spread info about the absence of any confidentiality with any email provider and in the mean time educate youself reading snowden's materials about nsa (kgb twin) deeds.
just wonder what do you mean by "detect users avoiding censorship"?
d'you mean pgp encryption prosecuted by 'armed enforcement group'?
What is this harder way that
What is this harder way that uses the *nix way to send mail directly? Does it use the hosts file to resolve the recipient Unix host to an IPA? Doesn't that bypass Tor? Doesn't setting hostnames break anonymity? Or have I got that wrong ...
I think what russianin meant by "detect users avoiding censorship" is new Russian law that says you are not allowed to use means of encryption beyond what the Russian goverment can break. If they can't taint your e-mails with substitutions or insertions, that means you broke the law and you go to jail.
Hi, TOR network is blocked
Hi, TOR network is blocked for me, so is all other pages of tor website except for the blog. Could anyone provide me any non "tor" related link where I could read about using pluggable transports? even the bridge is not working for me, and so is orbot on android. Plese help.
How do we tell between a
How do we tell between a censored user genuinely asking for help in figuring out Pluggable Transports, and an agent of a censor pretending to be such just to find out what and where the latest PTs are so they can detect them?
Hi! If i use tor while
Hi! If i use tor while connected to a public wifi hotspot, will this defeat the purpose?
Can using tor help prevent somebody from accessing data that passes through the wifi router.
If accessible, how can i make the files appear "shredded" if the owner of this hotspot tries to access them, while still being able to view them in my browser.
I'm mainly interested in sending/receiving text and links.
1. you should force your tcp
1. you should force your tcp connection through tor proxy. the simplest way is to use tbb.
2. you should use onion sites.
so your inflight data cannot be accessed by anyone but the site owner.
It won't, provided you pay
It won't, provided you pay attention to some details.
Generally, the connection between your computer and your entry (guard) node is a triple layer of SSL encryption, so anyone accessing your data that passes through the wifi router will just see SSL. If they break that, they see more SSL.
The people who produce the TAILS OS write about other matters you must take into account. In particular:
- The problem of a free Wi-Fi network's captive portal:
https://tails.boum.org/doc/anonymous_internet/unsafe_browser/index.en.h…
- When to spoof your laptop's MAC (the macchanger command, only in *nix OSs):
https://tails.boum.org/doc/first_steps/startup_options/mac_spoofing/ind…
Can we change to use .i2p or
Can we change to use .i2p or Ar till Virtual private network service?
Even mega corps using Internet protocol or Muti protocol labering system was too expensive, CSCO , ASA and JNPR Junos is good idea, cheack point capulate Virtual private network both were mutational - Gov agency used firm
We should buy Small satellites broadband access or cheapest pi hardware (one time use) to bypass hardware GUID identification
All PRC/ROC make hardware motherboard like Gigabyte , ASUS(hong hai presentation ) , MSI , AAPL, Lenovo, MSFT , LG , Samsung , EVGA ,oracle, Citix,HTC,VMware have backdoor via south or north chips set placed already to remote turn on your camera , GPS chip , Mic to recording your face, voice ,location , etc