Tor at the Heart: The OONI project

During the month of December, we're highlighting other organizations and projects that rely on Tor, build on Tor, or are accomplishing their missions better because Tor exists. Check out our blog each day to learn about our fellow travelers. And please support the Tor Project! We're at the heart of Internet freedom.
Donate today
In this post we provide an overview of OONI, a project under The Tor Project.
The Open Observatory of Network Interference (OONI) is a free software project under The Tor Project that aims to increase transparency about internet censorship around the world. To this end, OONI has developed multiple free software tests (called ooniprobe) that are designed to examine the following:
- Blocking of websites;
- Blocking of Instant Messaging software such as WhatsApp and Facebook Messenger;
- Blocking of Tor, proxies, VPNs, and sensitive domains;
- Detection of systems responsible for censorship, surveillance and traffic manipulation.
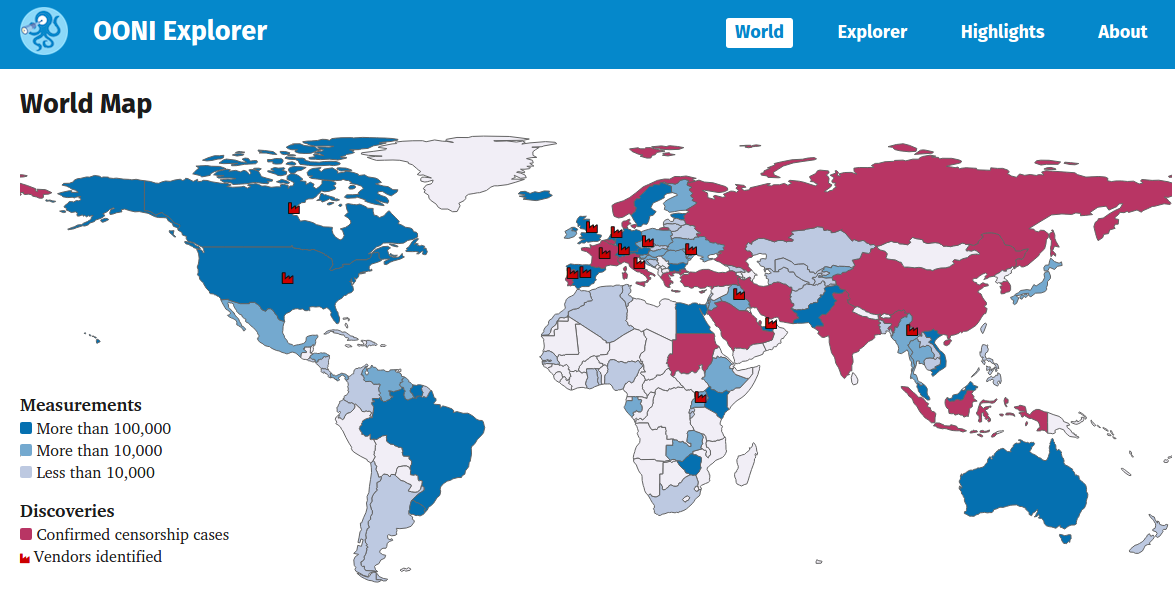
Anyone can run these tests to examine whether censorship is being implemented in their network. All data collected through ooniprobe is published and can serve as a resource for those who are interested in knowing how, when, and by whom internet censorship is being implemented. You can find OONI’s data in JSON format or via OONI Explorer: a global map for exploring and interacting with all the network measurement data that OONI has collected from 2012 to date.
Hundreds of volunteers have run ooniprobe across more than 100 countries around the world, shedding light on multiple instances of internet censorship. WhatsApp, for example, was found to be blocked in Brazil earlier this year, while Facebook and Twitter were censored during Uganda’s 2016 general elections. OONI data also shows that news websites were blocked in Iran and India, amongst many other countries, and that sites supporting LGBTI dating also appeared to be tampered with in Zambia.
OONI aims to equip the public around the world with data that can serve as evidence of internet censorship events. Such data not only shows whether a site or service was blocked, but more importantly, how it was blocked, when, where, and by whom. This type of information can be particularly useful to the following:
- Lawyers: Examine the legality of the type of internet censorship implemented in your country, and use OONI’s data as evidence.
- Journalists: Improve the credibility of your stories by referencing network measurement data as evidence of censorship events.
- Researchers: Use OONI’s data to explore new questions. Researchers from the University of Cambridge and UC Berkeley, for example, were able to examine the differential treatment of anonymous users through the use of OONI data.
- Activists, advocates, campaigners: Inform your work based on evidence of censorship events.
- Circumvention tool projects: Inform the development of your tools and strategies based on OONI’s findings on censorship events around the world.
To empower participation in censorship research, OONI has established partnerships with local non-profit organizations around the world. Some of these organizations include:
- Sinar Project (Malaysia)
- Coding Rights (Brazil)
-
Centre for Intellectual Property & Information Technology Law (Kenya)
-
Derechos Digitales (Chile)
-
Open Net Korea (South Korea)
-
The East and Horn of Africa Human Rights Defenders Project (Uganda)
These partnerships involve the daily collection of network measurements from local vantage points, determining which sites and services to test per country, and analyzing measurements within social, political, and legal context. Some partners, such as Sinar Project, even organize regional workshops to teach other groups and organizations how to measure internet censorship through the use of ooniprobe.
The Tor Project has supported the OONI project from day 1. Donate to The Tor Project today and help us continue to uncover internet censorship around the world.
Written by Maria Xynou, OONI’s Research and Partnerships Coordinator

Comments
Please note that the comment area below has been archived.
Great tools that showed me
Great tools that showed me that my supposedly free liberal
western europe country is using censorship.
Easy to set and run, those tools are essential to understand
the hows and when.
Best wishes.
For some reason I can not
For some reason I can not connect to the localhost:8842. Any suggestions?
Which version of ooniprobe
Which version of ooniprobe are you running (you can see this by doing ooniprobe --version)?
The web UI is supported in ooniprobe versions 2.0.0 and up.
As of this writing, all
-- https://www.crowdsupply.com/raptor-computing-systems/talos-secure-works…
Until such evil ends all programmers should go on strike indefinitely.
If the GCHQ/NSA insist on serving all companies with NSL gag orders that prevent people from owning their own computers, and the legal system has completely failed, then the only option left is to start bombing the spooks.
You've convinced me there is
You've convinced me there is cause for concern. Not panic, yet, but sufficient concern that I hope that EFF or other technical organizations will try to find persons with the requisite expertise to hunt for evidence that ME is being abused.
we hope using affordably Pi
we hope using affordably Pi 3 install those testing sensitive domain
equipment instant of expensive gaming Personal computer , can
developer per-built the software using .ova format for virtual box ,
so they we can buy 50-100 pi3 install rest of Asia via wireless N in
root top and PoE (power over Ethernet) run 7/24/365 to avoid seize by local-secret
political
police>_<
Finally those sensitive domain list in public may get those Router/
Switch / parents(censorship) control software to create a Database
and import those website format in multinational corp / Security
service for easy to identify that any ip/mac visit those website
We should advertising/marketing that software via gaming device
likes Xbox one / Play station pro / steam client / Dota 2 for more
user to know it instant of computer science PhD degree holder
Tried installing ooniprobe
Tried installing ooniprobe on Debian 8 system.
Observed some worrisome synaptic output during installation:
> ...
> (synaptic:****): GLib-CRITICAL **: g_child_watch_add_full: assertion 'pid > 0' failed
> ...
> WARNING: Passing command line arguments is deprecated
> ...
First installation failed (tcpdump not in the dependencies but should be?)
People installing ooniprobe
People installing ooniprobe will apparently get a file called ooni-resources.tar.gz from github.com. (I believe the file in question is the current geoip database.) This is worrisome because github has suffered a number of dangerous security breaches, some of which apparently yielded the login credentials of thousands of developers.
ooniprobe appears to have
ooniprobe appears to have installed successfully on my Debian 8 system after fixing some minor problems:
o I am using the onion service partial mirrors of the Debian repositories and the deb.torproject.org repository. Often I have some trouble connecting via the onion services, and to others trying this, I counsel patience, and if you have not fetched the file before synaptic times out, just try reloading again. After installing, I find, you often have to go through the process a second time in order to obtain a few debs which were missed on the first round. If you see a warning that you are about to install unauthenticated software, immediately cancel the download and try again later.
o for some reason it seems that tcpdump was not automatically installed so ooniprobe failed to run until I manually installed tcpdump.
Political dissidents
Political dissidents everywhere love CitizenLabs (from the Munk School of Journalism in Toronto, Canada) and I love the fact that OONI is working very closely with them to devise the censorship tests included in ooniprobe.
However, CitizenLabs appears to suffer from the same problem as Tor Project (until very recently):
o tiny staff, tiny budget, especially in view of their critical importance to democracy around the globe,
o funded by a FVEY government (Canada),
o (probably not by coincidence) focuses only on censorship and other abuses by governments which are not generally regarded as friendly towards the FVEY nations (US,UK,CA,AU,NZ).
I would like to urge OONI to remain on guard for censorship inside US and UK, because as the USG takes a sharp right turn towards something very much resembling a potentially genocidal fascism, some degree of explicit on-line censorship seems like the least nasty novelty which Americans may reasonably expect to experience in the coming years.
Looking through the
Looking through the CitizenLab tests included in ooniprobe, I don't see a test for USA. Shouldn't you have a US test, with sites such as wikileaks.org and the sites which a notorious Washington Post article designated (falsely) as "pro-Putin" [sic] "fake news" [sic] sites such as theintercept.com, techdirt.com, truthdig.com, truth-out.org*, etc. And some sites which I think could credibly be designated as "alt-right sites", such as infowars and prisonplanet and other Alex Jones sites.
* The notorious leak of John Podesta's email inbox showed that he somehow got signed up to receive email alerts to truth-out.org stories.
OONI is a wonderful project
OONI is a wonderful project and I support it wholeheartedly.
However, you probably should have mentioned that many cybersecurity researchers have grown increasingly concerned that owing to unresolved confusion in the talks seeking to update the Wassenaar acords which govern running any kind of network probes (such as ooniprobe) could potentially result in arrest for anything from "illegal export of a cyberweapon" to "espionage", which are very serious charges in most "Western democracies". On the bright side, anyone who experiences such a fate would probably get good legal help from ACLU, EFF, and other such organizations.
OONI is a wonderful
OONI is a wonderful project.
However, you probably should have highlighted the standard warning to read the "RISKS" page before installing ooniprobe.
Highlights from OONI's own "RISKS" page:
o ooniprobe by default will daily try to contact numerous controversial websites featuring porn, politics, and hate speech (in order to determine what kind of content is being censored),
o oooniprobe tests ordinary http connections, so your true IP address will wind up in the (daily) server logs in all kinds of controversial websites,
o by default the results will be sent (via hidden services) to OONI and published "anonymously",
o by default your ASN (internet provider), geolocation, and the timestamp of the test will be published, which is probably enough to deanonymize you.
It seems to me that this implies that:
o if an agency with global reach such as the US FBI raids a hate speech site in FR (for example) and finds your IP in their server logs, you are very likely to wind up in the watchlists of dozens of "Western" intelligence agencies and national police agencies
o if Russian intelligence finds your IP (which can sometimes be leaked in the published data although OONI tries to prevent this), consequences (even outside Russia) *may* include IRL harrassment or worse,
o if Ethiopian intelligence (for examples) finds your IP, consequences are *likely* to be severe.
Ooniprobe is fabulous, but the world is dangerous and very rapidly becoming much more so, with such former self-proclaimed defenders of human rights as UK and USA turning sharply towards alt-right style street violence and other ugly modes of repression.
That said, ooniprobe tests are divided between censorship tests (the ones involving contacting controversial websites) and interferrence tests (which check for things like packet injection). Further, it is apparently possible to configure ooniprobe to not run daily, and users can ask that their test results not be "anonymously" reported to OONI by onion service---but this might be more dangerous than letting your test results be published:
Currently, if an US intelligence agency detects you running ooniprobe, it might actually help your defense if a US LEA arrests you because your IP turned up in the server logs of some porn site. But this judgment is subject to rapid unpredictable flux as the incoming US administration starts to decide what kinds of specific policies to adopt.
I stress that OONI documents clearly state that to their knowledge, no resident of a "Western democracy" has yet suffered arrest as the result of running ooniprobe. But as more and more US LEAs rush to arrest people using increasingly flawed electronic evidence, confusion owing to the chaotic sharing of flawed data is rapidly increasing, and I fear it is virtually certain that running ooniprobe will turn out to be too dangerous for anyone who does not have a good lawyer on retainer.
I say this not to criticize,but only just to discuss ways to improve our game.
But the US and the EU ar
But the US and the EU ar blocking pirate websites. Why are not they red?